Radio communication is regarded as the main vulnerability of wireless security systems. It can presumably be easily jammed using equipment that can be purchased “at every corner,” and without radio communication, the alarm system is deprived of the opportunity to resist the intruders. Consequently, the facility becomes defenseless.
This article dispels the myths about jammers, talks about their real capabilities, and how counteraction is implemented in Ajax for this type of sabotage.
How radio communication is “jammed”
Jamming represents unlawful creation of interference within radio channels. It is used to prevent communication of alarms within wireless security systems. Devices for jamming are called interference generators or signal suppressors and they are commonly known as jammers.
Interference generators operate within a specific radius at the frequency of the device whose operation is to be disturbed. If the frequencies of the device and the jammer do not match, the jamming will not affect the operation of the device.
Jamming can be aimed at both individual detectors and the security system as a whole.

Jamming attempts occur relatively rarely, i. e. not more than 5 cases per year per 20,000 protected facilities. This is attributed to the fact that home burglaries at the premises equipped with alarm systems last under 2 minutes. Jamming is inexpedient in this case as it only delays the process.
What types of jammers exist

Interference generator can “jam” a certain band or be broadband sabotaging several communication technologies of security systems simultaneously.
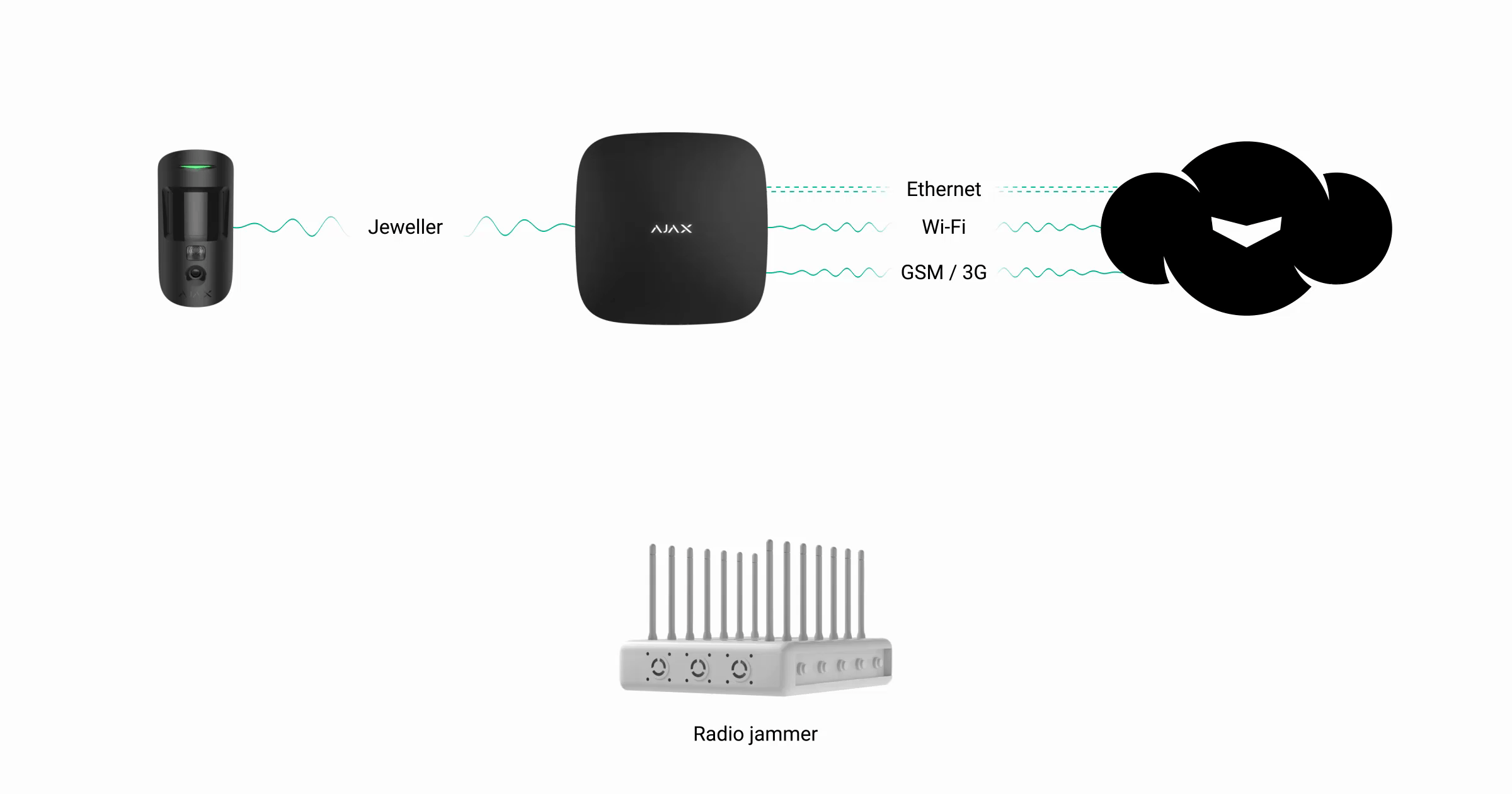
For example, Ajax uses 5 frequency bands for communication:
- 2G/GSM (900/1800 MHz), 3G/UMTS (2100 MHz), and LTE (900/1800/2600 МHz depending on the region of sale) networks of cellular operators
- Wi-Fi network (2.4 GHz)
- Jeweller radio communication (868.0–868.6 MHz or 868.7–869.2 MHz depending on the region)
Broadband interference generators that can jam several networks at once (for example, Wi-Fi and GSM) can be:
- Hand-held or portable with the size of a phone and relatively low power; therefore, they prevent data transmission at a distance of 5-15 meters (without obstacles).

- Stationary— such appliances are much more powerful and expensive. The higher the price, the greater the range and number of networks that they can jam. The wider the frequency band and the larger the jamming radius, the more powerful the interference generator must be. Powerful jammers can become very hot, and they require additional cooling. Also, the lower the jamming frequency, the larger the size of the interference generator antenna must be. All this affects the dimensions of the device, and jammers with a range of 100 meters (in open space) have considerable dimensions, need forced cooling, and power supply of 230 V.

- Self-made — as a rule, low-power jammers that operate over short distances. In order to increase the jamming coverage, expensive broadband amplifiers are required, and the creation of such equipment involves specialized skills.

How the Ajax security system responds to jamming
Hub uses GSM and Ethernet for connection to Ajax Cloud service and for the transmission of alarms to the user and the security company, and Hub 2 Plus is unique among the security system control panels — it uses four authorized communication channels at the same time: Wi-Fi, Ethernet, and two 2G/3G/LTE SIM-card slots. For communication with security system devices hub uses Jeweller radio technology.
1. GSM channel jamming
GSM channel jamming can only be successful if the GSM signal strength is weak. A strong signal is almost impossible to jam due to the high power of the transmitter tower of a cellular operator.
When communication through the GSM channel is lost, “1” is added to the fault counter (red badge) on the hub icon in the Ajax app.
Meanwhile, the hub continues to function properly via Ethernet (and/or Wi-Fi in Hub Plus/Hub 2 Plus). If other communication channels are unavailable or disconnected, the hub loses connection with the server that sends an alarm to the users of the security system and the security company. Meanwhile, the system continues to operate offline logging detector alarms and sending corresponding alerts using HomeSiren / StreetSiren / StreetSiren DoubleDeck sirens.
Once the connection is restored, all alarms will be delivered to the application and the security company.
2. Jeweller frequency jamming
The hub and the devices connected to it constantly measure the noise level in the radio channel at Jeweller frequencies.
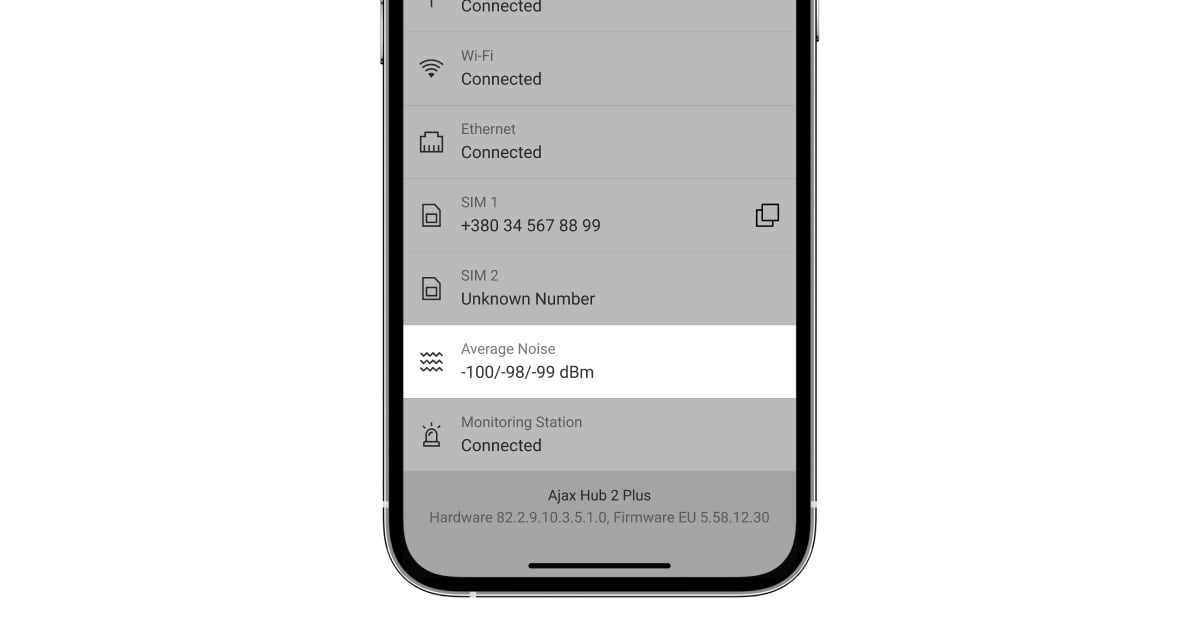
The Ajax security system detects jamming if the noise power level exceeds -70 dBm over 30 seconds. After that, the hub automatically sends a jamming notification to all users and the security company. Consequently, in order to avoid the loss of connection, the hub switches to a less noise-polluted frequency.
Meanwhile, if the hub loses communication with the detector or the device, it sends the corresponding notifications to the users of the security system and the security company.
Jamming can be detected not only by hubs, but also by radio signal range extenders.
3. Wi-Fi jamming
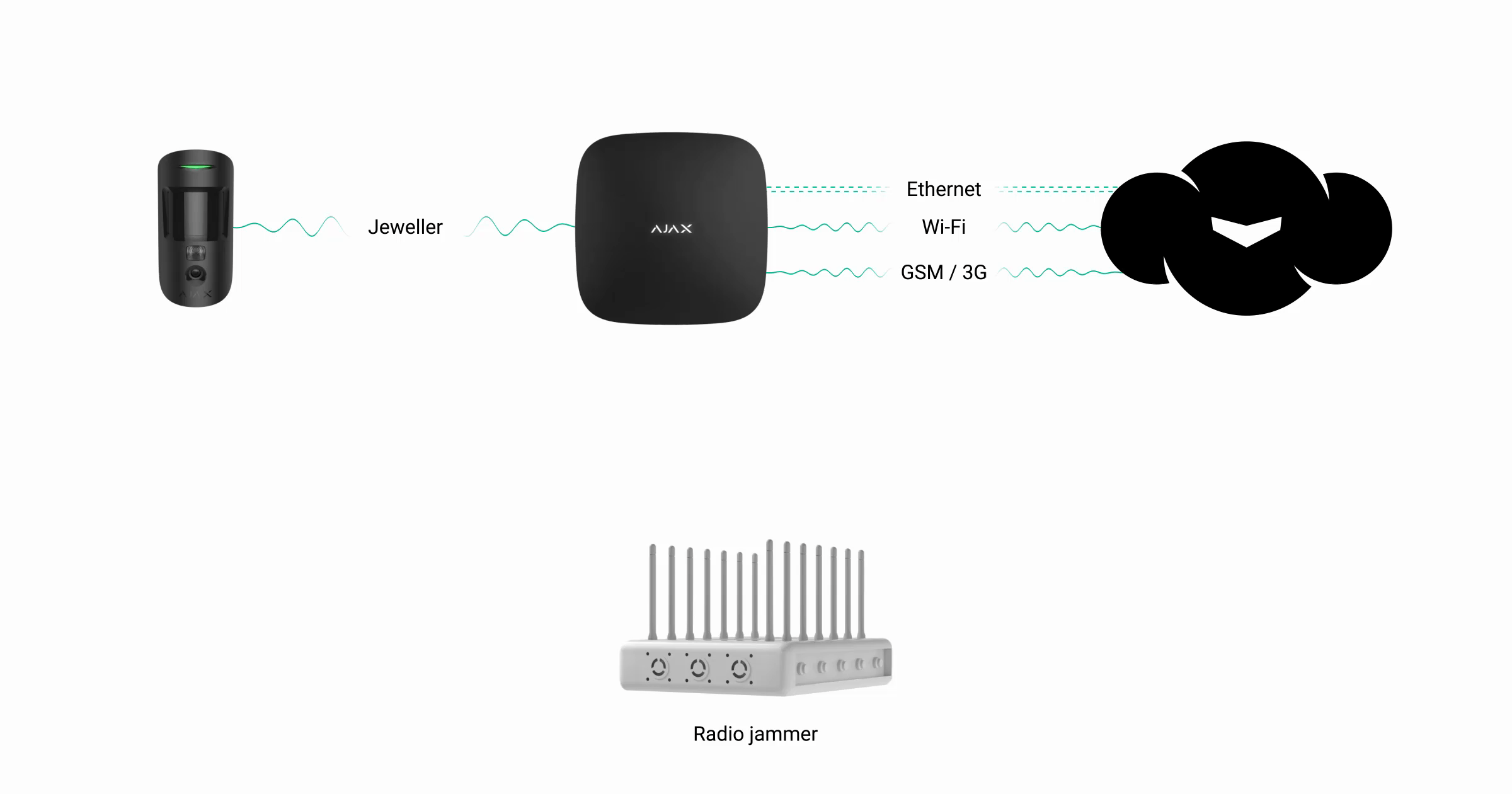
When jammed, Hub Plus continues to operate properly via Ethernet and SIM-card if these communication channels are used. When Wi-Fi is lost, “1” is added to the fault counter (red badge) on the hub icon in the Ajax app.

If other communication channels are unavailable or disconnected, the hub loses communication with the server that sends an alarm to the users of the security system and the security company. Meanwhile, the system continues to operate offline logging detector alarms and sending corresponding alerts using HomeSiren / StreetSiren / StreetSiren DoubleDeck sirens.
4. GSM, Wi-Fi, Jeweller jamming
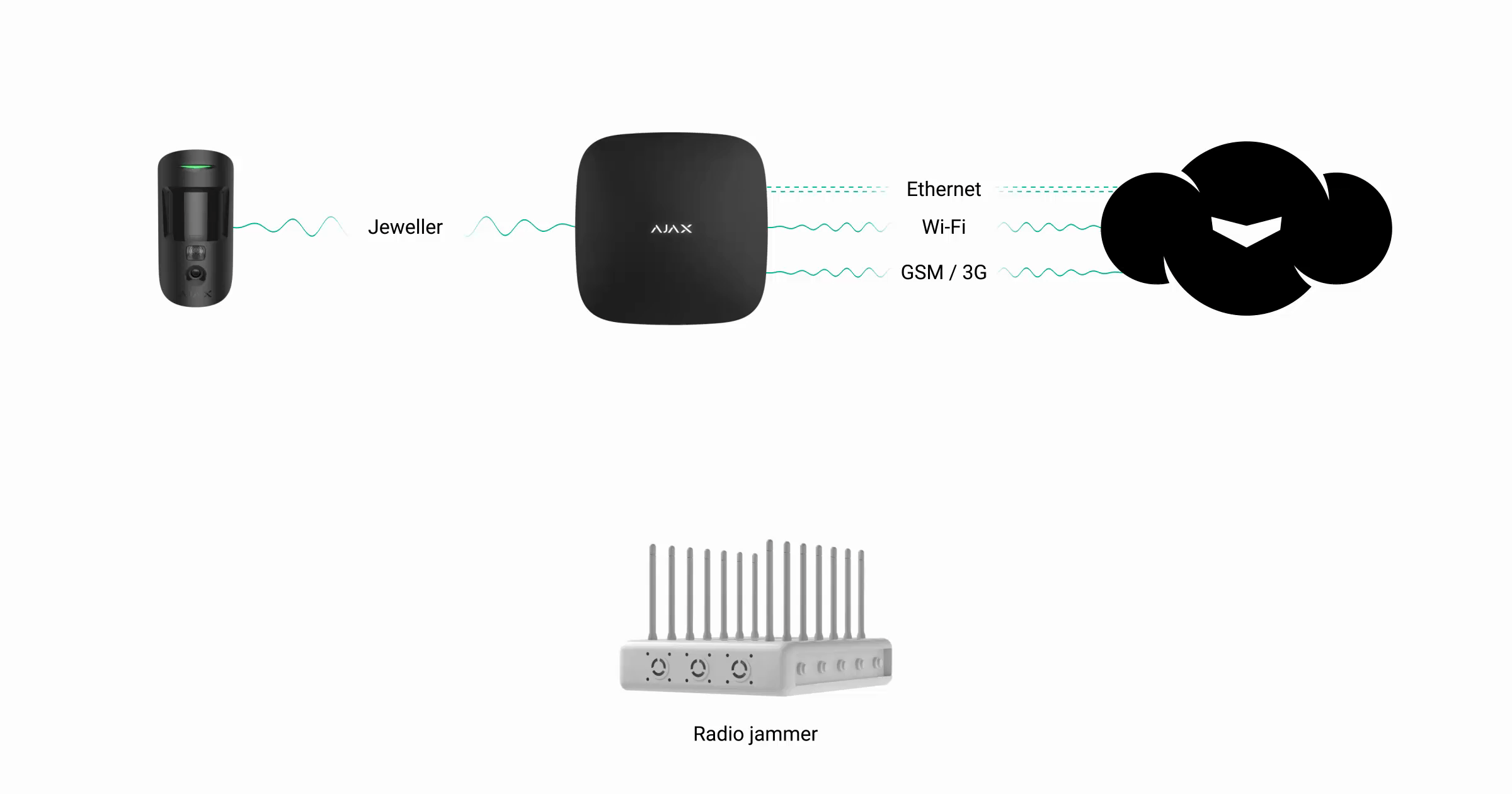
Interference generators capable of jamming 2G/3G/LTE, Wi-Fi, and Jeweler bands at the same time over a large area (with allowance for the walls, ceilings, and objects that reflect signals inside the premises) are overall and expensive devices that are not available commercially.
However, if the robbers have such a broadband interference generator, the Ajax security system will detect a high noise level at Jeweller frequencies and will send the appropriate alerts to the users and the security company via Ethernet (if connected). In the Ajax apps, you will see that connections via Wi-Fi and 2G/3G/LTE networks are inactive. If the Ethernet connection is absent, the hub will lose communication with the server. The server will report the problem by sending an alert to the users of the security system and the security company.
How to protect the security system from jamming

1. Install the hub in a place hidden from third parties, away from doors and windows. During installation, remember that the location of the hub must ensure a stable signal strength for all Ajax devices.
2. Use all available communication channels.
If you have Hub: SIM-card and Ethernet.
If you have Hub 2: two SIM-cards from different providers and Ethernet. If Ethernet is lost, the hub switches to the SIM-card. If data don’t pass via the mobile Internet, the hub engages the second SIM-card. It takes up to 4 minutes to switch SIM-cards, while the standard for security systems is 17 minutes.
The use of two SIM-cards will not protect against GSM jamming (since both SIM-cards use the same frequencies) but it helps in cases when one of the SIM-cards stops responding for whatever reason. For example, due to a failure on the side of the cellular operator.
If you have Hub Plus or Hub 2 Plus: two SIM-cards provided by different operators supporting 3G (LTE for Hub 2 Plus), Ethernet, and Wi-Fi from different access points using Internet from different providers.
If Wi-Fi and Ethernet connections are lost, Hub Plus/Hub 2 Plus switches to SIM-card and uses 3G (or LTE for Hub 2 Plus) network. If the data are not transmitted through the 3G/LTE Internet, the hub switches to 2G within seconds. If the problem is not resolved, it uses the second SIM-card following the same logic: 3G/LTE as the main network and 2G as a backup one. Moreover, it takes up to 4 minutes to switch SIM-cards, while 17 minutes represents the standard for security systems.
The use of two SIM-cards will not protect against GSM jamming (since both SIM-cards use the same frequencies) but it helps in cases when one of the SIM-cards stops responding for whatever reason. For example, due to a failure on the side of the cellular operator.
In the majority of cases, criminals act according to the following scheme:
1) Turn on a jammer.
2) Break into the facility.
3) Find the security system control panel and disconnect the main and backup power supplies.
4) Hide nearby and wait for the response from the security company.
If there is no response from the security company, the thieves begin to pilfer everything.
Summary:
- Jamming of all available radio communication channels of professional security systems over a large area can only be achieved using overall and expensive interference generators.
- A reliable security system does not rely on a single channel of wireless communication with the outside world, and a wireless connection should supplement the wired connection to the Internet.
- Even if intruders succeed in complete isolation of a professional security system, you and the security company will be informed of the situation — due to scheduled security system polling by server.
- If communication with the security system is lost, you should arrive at the facility as soon as possible. Security companies send rapid response teams in such cases immediately.



